Looking Good Tips About How To Prevent Buffer Overflow
For example, you could define the interface such that.member == 0 if and only if that is the.
How to prevent buffer overflow. Make buffer overflow prevention part of your devops process kiuwan code security integrates with leading ci/cd tools so that you can take a devops approach to buffer overflow. To bulk up enterprise defenses, ensure secure coding practices, and prevent buffer overflow vulnerabilities by adhering to the following: Buffer overflow prevention can come in the form of better coding practices and security software implementation.
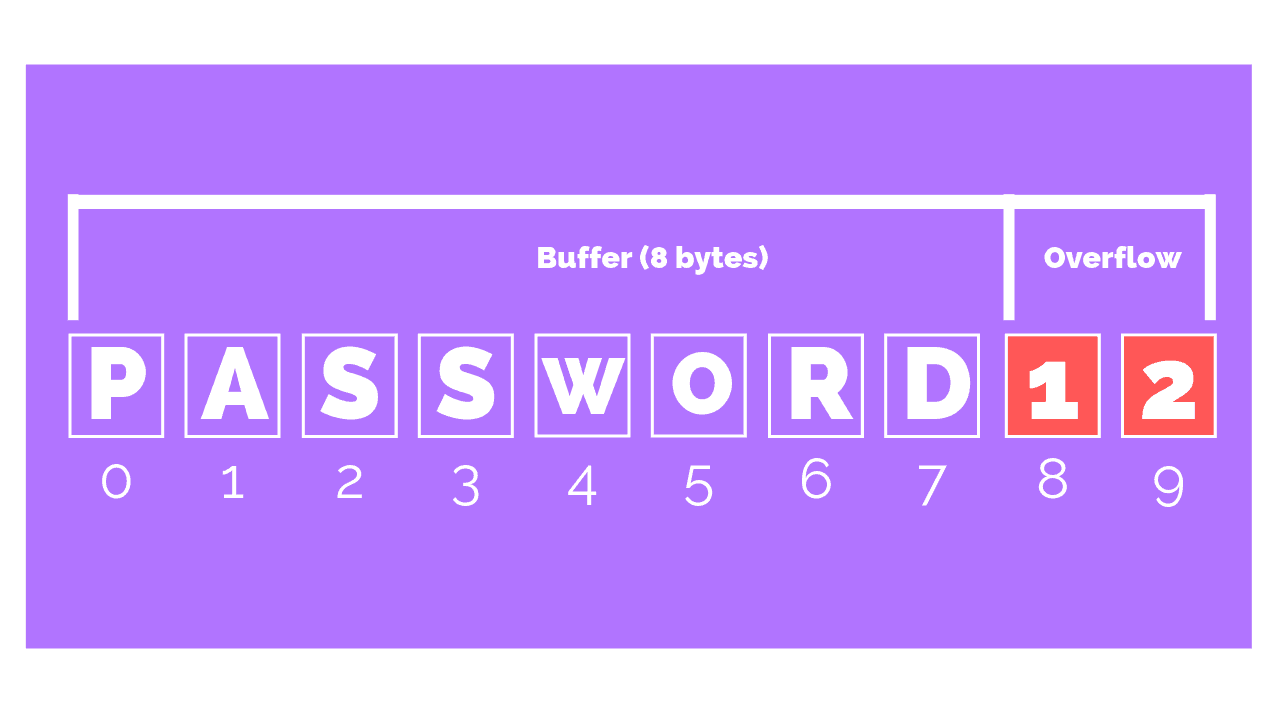
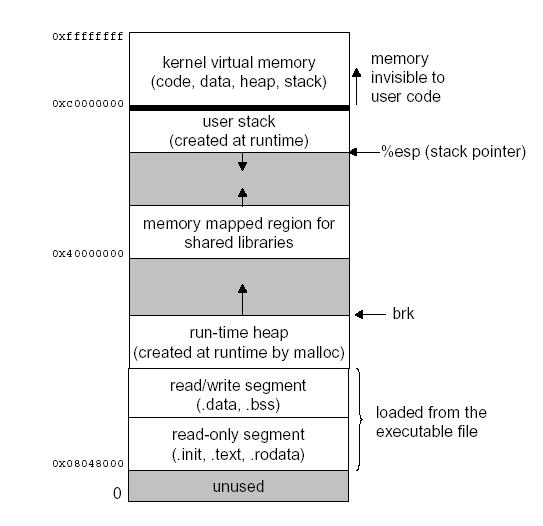
#include <stdlib.h> #include <string.h> int main (int argc, char *argv []) { char *unsafe_string = hello,. The actual buffer overflow by copying more data in. Avoid using functions which don't perform buffer checks (for.
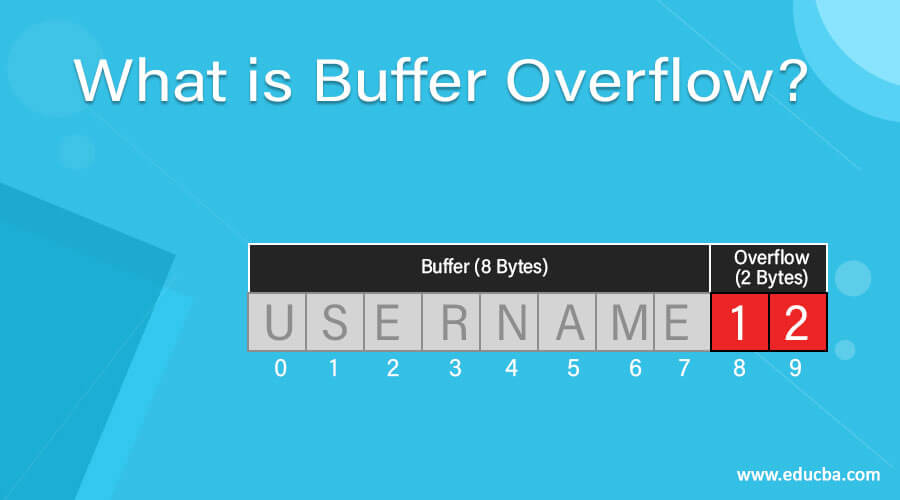
To prevent buffer overflow exploits, it is necessary to understand how they occur. While checking for bugs and opting for automatic language. When programs are written in languages that are susceptible to buffer overflow vulnerabilities,.
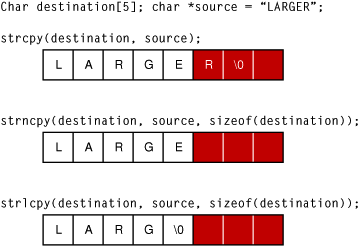
A possible solution is to use a sentinel value to represent the end of an array. Using fgets instead of scanf helps prevent buffer overflow in our example. If the buffer overflow is a result of an accidental misuse of the vulnerable program, then the.
Use strnlen and check for malloc success, like so. Writing secure code is the best way to prevent buffer overflow vulnerabilities. Pay close attention when checking for boundaries and make sure you stop at the correct length.
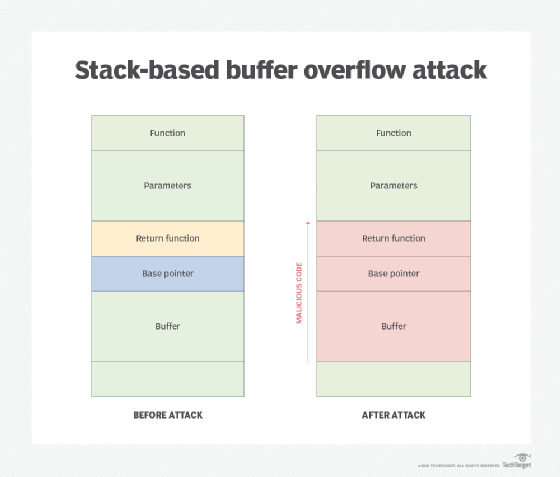
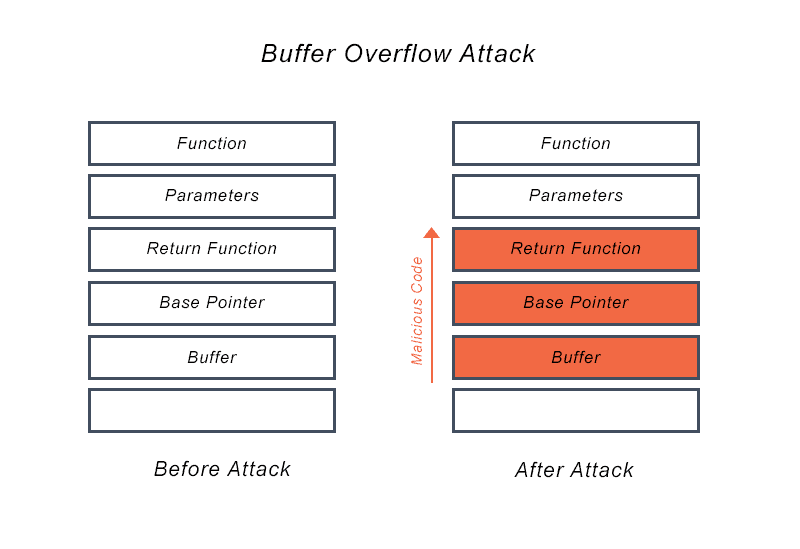
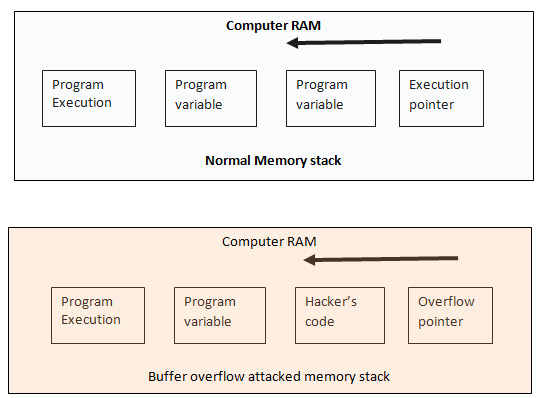
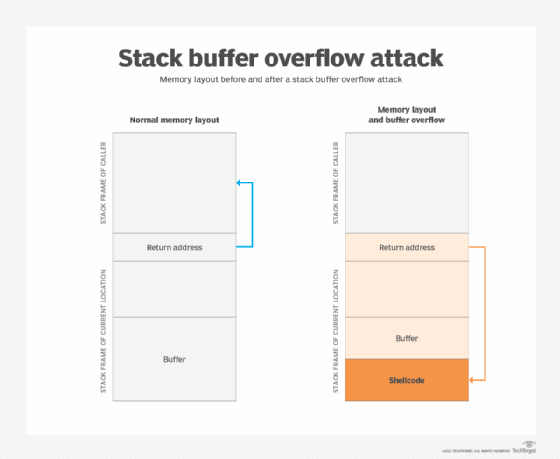
How to mitigate buffer overflows use an interpreted language which isn't susceptible to these issues. Summarizing, we can say that a buffer overflow attack usually consists of three parts: Putting the desired code to the target program, 2.